 Federal Office for Migration and Refugees (BAMF)
· Source
Federal Office for Migration and Refugees (BAMF)
· Source
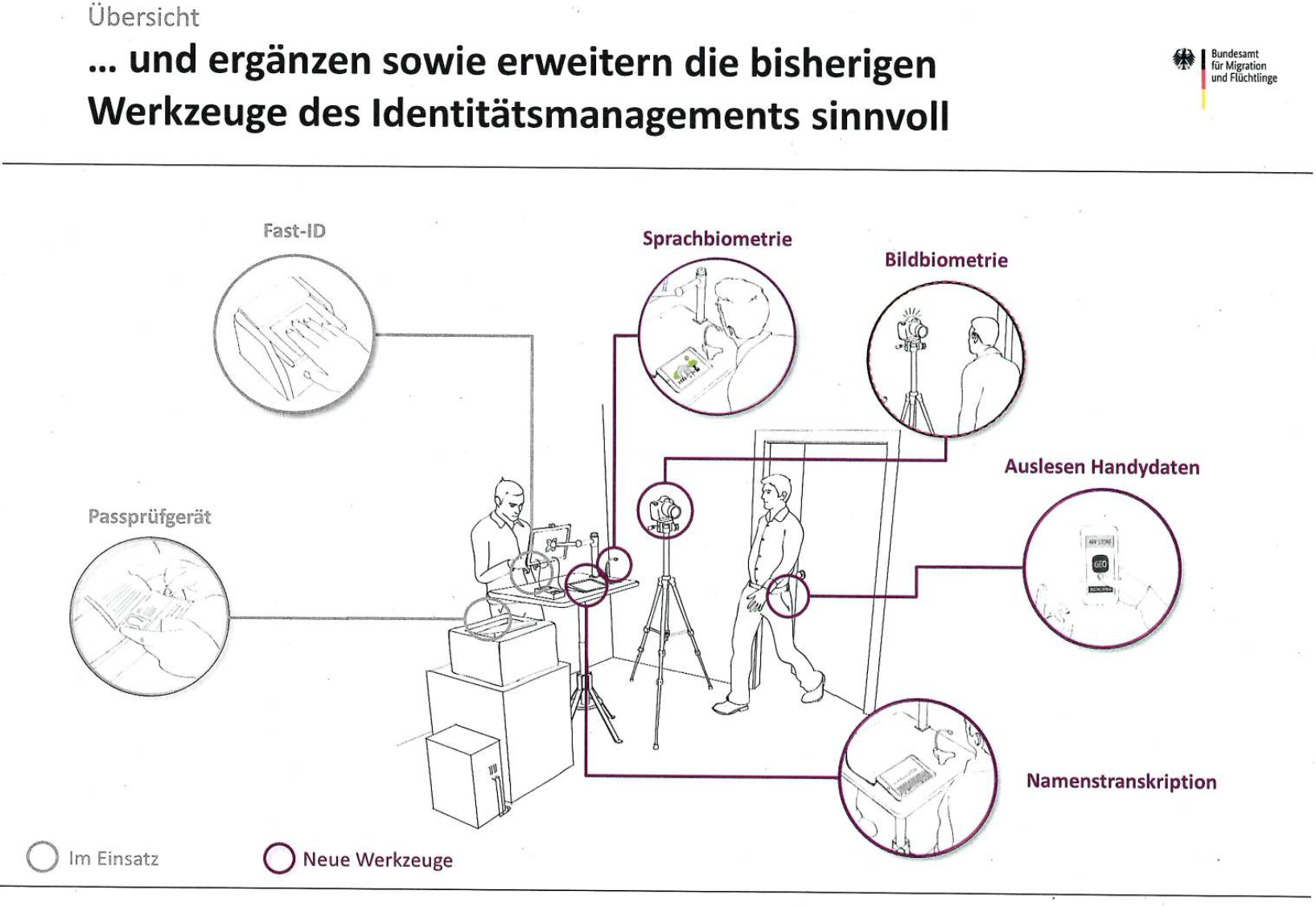
Establishing the identity of asylum seekers in the absence of credible documents represents a significant challenge for governments. To support decision-making processes in identity determination and verification procedures, Germany’s Federal Office for Migration and Refugees introduced three digital identification systems under the “Integrated Identity Management - plausibility, data quality and security aspects (IDM-S)” programme.
Because these algorithmic systems are deployed in highly political settings affecting vulnerable populations on the move, this research investigates how the Federal Office legitimises the policy and use of IDM-S that indicate a new direction of governance driven by so-called “innovative technologies”.
The study is grounded in legitimacy theory - considered a core virtue of just institutions and their exercise of public authority, hence, power over individuals. Legitimacy is understood as a justificatory concept seen in conjunction with (good) governance, the processes of making and implementing decisions by considering human rights frameworks - in this particular case the right to privacy as protected under Art 17 ICCPR.
»Download report here (via Leuphana University)«
Analysis methods and data sources
To account for the multiplicity of digital systems in governance that influence decision-making, this research applies an analytical tool-mix. The data justice framework is applied to structure the evaluation of state practices. In addition, the qualitative content analysis is used to find patterns in publicly available documents.
The following data sources were used for analysis:
- internal documents of the Federal Office, such as instructions for identity determination procedures, handbooks on the three studied IDM-S systems and training manuals for employees
- press releases, the Federal Office’s Digitalisation Agenda 2020 and published interviews with its leadership
- policy documents, such as proposed legislations and draft laws, protocols of parliamentary debates and the public hearing procedure, written statements of civil society organisations and legal experts
- answers to so-called “kleine Anfragen” (small requests) of opposition parties
Four expert interviews were carried out to include (some of the known) experiences of affected individuals and to verify identified information provided by the government. Hence, this research would not have been possible in the same extent without the contribution of the interviewed experts.
Special thanks to Bellinda Bartolucci (PRO ASYL), Lea Beckmann (GFF) and Anna Biselli for providing valuable input for this paper. Additional thanks to the Office of the Federal Commissioner for Data Protection and Freedom of Information (BfDI) for the written statements on the subject.
Key findings
The results underscore profound discrepancies between justifications and state practices, outlining severe privacy violations as well as the lack of compliance to qualitative values in governance that pertain to participation, transparency, accountability, impartiality and scientific soundness of state operations.
The results of the analysis revealed four main justification patterns:
- The references to the rule of law and shared public beliefs implied that both policy and practice followed legal standards perceived as necessary to protect society from security threats.
- Information that could potentially delegitimise state conduct was not disclosed whereas proactive communication by authorities was largely positive to demonstrate successful operations. At the same time accountability was limited.
- The emphasis on efficiency and IDM-S’ high level of innovation implied the usefulness of the digital systems stemming from their easy application, cost and time efficiency, as well as the ability to produce fast results. Innovation and agility underlined the self-proclaimed image of a modern, tech-savvy administration.
- The last pattern portrayed efforts to uphold the impression of rational and objective governmental operations based on the mathematical-technical approach used to generate the systems’ results.
Ultimately, the findings encourage searching for better alternatives to the currently applied tech-heavy programme - alternatives that are firmly grounded in democratic governance principles and that adequately account for asylum seekers’ right to privacy as well as their vulnerable status.